Browser distrust events of WebPKI Certificate Authorities occur on average approximately every 1.23 years. These events highlight the critical role the WebPKI plays in maintaining secure communications on the internet and how failures within this system can have far-reaching implications. By examining these incidents, we can identify common patterns and underlying causes that lead to distrust, so as implementors and operators, we don’t end up repeating the same mistakes.

Identifying Common Patterns
As they say, those who don’t know history are destined to repeat it, so it is worthwhile to take a look at the history of CA distrust events to understand what, if any common patterns exist:
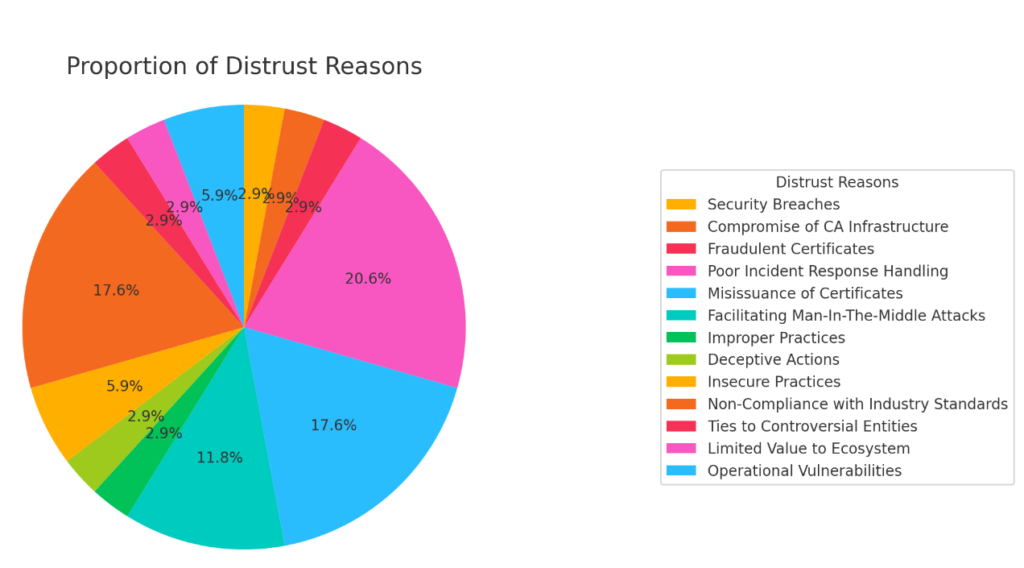
- Security Breaches: Involves unauthorized access to the CA’s infrastructure, leading to potential misuse of certificate issuance capabilities.
- Compromise of CA Infrastructure: Refers to breaches where the core infrastructure of the CA is compromised, resulting in unauthorized certificate issuance.
- Fraudulent Certificates: Occurs when certificates are issued without proper authorization, often leading to the impersonation of legitimate websites.
- Poor Incident Response Handling: Indicates that the CA failed to adequately respond to security incidents, exacerbating the impact of the initial problem.
- Misissuance of Certificates: Happens when CAs issue certificates incorrectly, either to the wrong entities or without proper validation, undermining trust.
- Facilitating Man-In-The-Middle Attacks: Refers to situations where misissued or improperly handled certificates enable attackers to intercept and alter communications.
- Improper Practices: Includes actions by CAs that deviate from accepted standards and best practices, leading to security risks.
- Deceptive Actions: Involves deliberate misleading actions by CAs, such as backdating certificates or other forms of dishonesty.
- Insecure Practices: Encompasses practices by CAs that fail to maintain adequate security controls, leading to vulnerabilities.
- Non-Compliance with Industry Standards: Indicates that the CA has repeatedly failed to adhere to industry standards and guidelines, leading to a loss of trust.
- Ties to Controversial Entities: Involves associations with entities that raise ethical or security concerns, leading to distrust.
- Limited Value to Ecosystem: Indicates that the CA does not provide significant value to the security ecosystem, often due to questionable practices or minimal compliance.
- Operational Vulnerabilities: Refers to weaknesses in the CA’s operational security, such as using default passwords or having exposed administrative tools, making them susceptible to attacks.
Browser Distrust Events
- DigiNotar (2011):
- Event: DigiNotar was hacked, leading to the issuance of fraudulent certificates. This prompted Mozilla, Google, and Microsoft to revoke trust in DigiNotar certificates.
- Labels: Security Breaches, Compromise of CA Infrastructure, Fraudulent Certificates, Poor Incident Response Handling
- Details: Mozilla Security Blog, Threatpost
- TurkTrust (2013):
- Event: It was discovered that TurkTrust mistakenly issued two intermediate CA certificates, one of which was used to issue a fraudulent certificate for *.google.com. This led to the distrust of the TurkTrust CA by major browsers.
- Labels: Misissuance of Certificates, Facilitating Man-In-The-Middle Attacks
- Details: Krebs on Security
- ANSSI (French CA) (2013):
- Event: It was discovered that ANSSI had issued a certificate to a network appliance company, which used it to inspect encrypted traffic. This led Google to revoke trust in the intermediate certificate.
- Labels: Misissuance of Certificates, Facilitating Man-In-The-Middle Attacks
- Details: Google Security Blog, Mozilla Blog
- CNNIC (China Internet Network Information Center) (2015):
- Event: CNNIC was distrusted after it issued an intermediate certificate to MCS Holdings, which misused it to issue unauthorized certificates.
- Labels: Misissuance of Certificates, Facilitating Man-In-The-Middle Attacks, Improper Practices
- Details: Tom’s Hardware, Mozilla Security Blog, Mozilla Security Blog
- WoSign and StartCom (2016):
- Event: WoSign (and StartCom) were distrusted after discovering multiple security issues, including backdating certificates, lying, and improper issuance.
- Labels: Misissuance of Certificates, Deceptive Actions, Insecure Practices
- Details: Tom’s Hardware, Google Security Blog
- Symantec (2017):
- Event: Google announced a gradual distrust of Symantec certificates due to numerous instances of certificate misissuance, impacting millions of websites.
- Labels: Misissuance of Certificates, Non-Compliance with Industry Standards, Poor Incident Response Handling
- Details: Bleeping Computer, Google Security Blog
- Certinomis (2019):
- Event: Mozilla distrusted Certinomis due to numerous incidents of misissuance and poor handling of security concerns.
- Labels: Misissuance of Certificates, Facilitating Man-In-The-Middle Attacks
- Details: Venafi Blog
- PROCERT (2020):
- Event: Mozilla distrusted Procert due to numerous incidents of misissuance and poor handling of security concerns.
- Labels: Non-Compliance with Industry Standards, Poor Incident Response Handling
- Details: Venafi Blog
- TrustCor (2022):
- Event: TrustCor was distrusted due to concerns about its ties to companies linked to the US intelligence community and its failure to provide satisfactory responses to these concerns.
- Labels: Ties to Controversial Entities, Limited Value to Ecosystem
- Details: gHacks, SSLs.com, SSL Shopper
- Camerfirma (2021):
- Event: Mozilla and Google removed trust in Camerfirma due to a series of compliance issues and failure to maintain industry standards.
- Labels: Non-Compliance with Industry Standards, Poor Incident Response Handling
- Details: The Register
- Visa (2022):
- Event: Issues include incomplete security audits that are required according to the
- Labels: Non-Compliance with Industry Standards, Poor Incident Response Handling
- Details: Feisty Duck
- e-Tugra (2023):
- Event: e-Tugra was distrusted due to security concerns. A researcher found numerous vulnerabilities in e-Tugra’s systems, including default passwords and accessible administrative tools, leading to a loss of trust.
- Labels: Operational Vulnerabilities, Insecure Practices, Poor Incident Response Handling
- Details: Sectigo, GitHub, Ian Carroll’s Blog
- Ecommerce CA (EU) (2024):
- Event: The Ecommerce CA in the EU faced browser distrust due to various security and compliance issues, leading to its removal from trusted lists.
- Labels: Non-Compliance with Industry Standards, Operational Vulnerabilities, Poor Incident Response Handling
- Details: EuroCommerce, Ecommerce Europe
- Entrust (2024):
- Event: The Chrome Security Team announced the distrust of several Entrust roots due to a pattern of compliance failures and unmet improvement commitments.
- Labels: Non-Compliance with Industry Standards, Poor Incident Response Handling
- Details: Google Security Blog
Conclusion
The frequency and patterns of browser distrust events underscore the critical importance of preventive measures, transparency, and effective incident response.
Implementing robust security practices, conducting regular audits, and maintaining compliance with industry standards can significantly reduce the risk of such incidents. Transparency in operations and public disclosure of security issues foster an environment of accountability and trust.
An ounce of prevention is indeed worth more than a pound of cure. By focusing on proactive measures and cultivating a culture of continuous improvement, Certificate Authorities can better navigate the complexities of WebPKI. Effective crisis communication and incident response plans are essential for managing the fallout from security breaches and maintaining the trust of users and the broader web community.
By learning from past incidents and addressing their root causes, we can work towards a more secure and resilient internet, where trust in the WebPKI system is consistently upheld. The collective effort of CAs, browser vendors, and security researchers will play a pivotal role in achieving this goal, ensuring the integrity and reliability of our online ecosystem.