I love security people, were paranoid, were fun, we think outside of the box but we are also human and often times get distracted by dogma and shiny objects. I think this happens a lot when talking about stuff like fingerprint based authentication.
The technology has a very big brother feel to it after all for most people only ever get fingerprinted when you’re registering with the government – hopefully because you want to go on a trip, not because you’re being sent up the river.
Unfortunately attackers don’t usually have this problem, the reason is their goals are more specific – they want in and if they are any good they quickly identify when a path they are perusing isn’t going to be effective so they move on to the next attack vector until they are in or exhaust all their options.
When we look objectively at a fingerprint based authentication solution like is being provided by Apple what are the weakness an attacker is going to go after?
First its useful to understand how these systems usually work, for those of you who have not read my last post here is a quick recap:
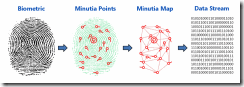
A picture is taken of the finger, the picture is converted to the set of features that are extractable from the picture, and those features are stored in something called a template. On use this process is repeated and the features are compared if enough match it must be you. Since its you your password or pin is released to a process to use it on your behalf.
The attacker here starts on the tail end of this process, he sees that in the end we are just taking about a password or pin – if this biometric mechanism is just an option and we can still use the password or pin we have not raised the security bar.
But what if the biometric is releasing access to a key or a strong password instead of your regular old password or pin? Then the attacker would probably start to ask the question how strong is a fingerprint compared to a password? Here is a good post summarizing the effective strength of a fingerprint based biometric – long story short it’s about the same as a six character password.
But wait, why go through the front door if the backdoor is open? For the attacker to execute this attack they have to have physical access to the device right? And the first rule of computer security is that if the attacker has physical access to your device its not your device any longer.
With the device in hand some other things the attacker would want to know are:
- How the matching works, is it done in software or hardware?
- What about where the template is stored? How is access to read and write the template accomplished?
- How is the template secured at rest? Is it readable? Can it be modified?
- What about where the password and pin is stored? Is it readable? Can it be modified?
- Does all of this happen in a single piece of hardware or is it shared across multiple devices?
- If its multiple devices, how do they authenticate each other if at all?
- How is access to the hardware doing the work authenticated? Is the software authenticated in any way?
- How about the integrity of the operating system, is there some mechanism that provides guarantees about its running state?
This isn’t an exhaustive list but gives you an idea of the problems here, they are core operating system problems which means that if you use this capability on a jail-broken device you are probably reducing your security above and beyond where you would have been otherwise.
As you can probably see its likely that the security of this solution isn’t going to be based on how good the sensor is at detecting fakes but how the overall system itself was architected.
So what do I think about the use of biometrics given the issues discussed here? I actually believe its possible to design, build and deploy a system that is reasonably secure based on this technology and that if done right you can measurably improve the security for the user.
It doesn’t need to be perfectly secure to do that either, you simply have to get the user to the point where he you can use long and strong passwords and not the sort of thing that they normally use:
For example in Windows one might rely on the following:
- UEFI secure boot ensures the boot loader is authenticated and non-tampered.
- Windows Secure boots only authenticated non-tampered code is loaded.
- Driver signing ensures all drivers are authenticated and non-tampered.
- Bitlocker ensures the disk is encrypted and cannot be modified outside the scope of the machine.
- The TPM ensures the Bitlocker keys are secured from the average attacker.
- Password Policies ensure passwords are sufficiently long and complicated.
- Reversibly encrypted passwords are stored using a strong key hierarchy where the root of the hierarchy is protected by the TPM.
- Fingerprints make it possible for the user to successfully log on with the long complicated passwords efficiently.
- Use sensors with reasonable fake finger and liveness tests.
There are still attacks in the above configuration but the low hanging fruit have been nailed and deploying a solution like this likely raises the bar an attacker has to cross to successfully exploit your environment.
Is it as good as other mechanisms (for example smart cards) certainly not, but better than what people actually do in production environments today? Yes, very likely.
Is this for everyone? Certainly not; but for many it would be a step up.
I am not familiar enough with the security architecture of the iPhone and OSX to say if the same sort of protections exist, they may – but without them one thing is for sure the “gummy bear attack” is probably the least of your worries.