The Windows platform for validating X.509 certificates has a feature I don’t see many discuss — its robust logging subsystem.
This allows a non-developer (and developers) to get insights into what is happening with applications interactions with CryptoAPI 2 and to some degree what is happening inside those APIs.
To use this feature you must first enable it, the easiest way to do that is via the EventViewer Management Console (eventvwr.msc), once in there you must navigate to the CryptoAPI 2 (CAPI2) node of the viewer:
![clip_image001[6] clip_image001[6]](https://unmitigatedrisk.com/wp-content/uploads/2013/03/clip_image0016_thumb.png) |
![clip_image002[6] clip_image002[6]](https://unmitigatedrisk.com/wp-content/uploads/2013/03/clip_image0026_thumb.png) |
![clip_image003[6] clip_image003[6]](https://unmitigatedrisk.com/wp-content/uploads/2013/03/clip_image0036_thumb.png) |
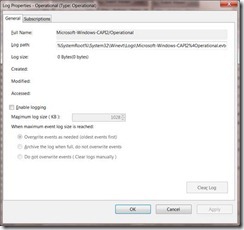
Once you get there you select Properties on the operational log, which will give you a dialog that looks something like this:
Once you “Enable Logging” and “Apply” the changes, immediately all calls to CryptoAPI will be logged. CryptoAPI is used all the time so by the time you close that dialog you will have some events you can look at:
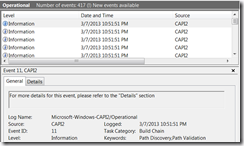
The high level view of each event doesn’t tell you much, for example in the above picture we really only know that the action that was being performed with a “Build Chain”, this particular event corresponds to a call to CertGetCertificateChain.
To really understand what is going on you need to look at the Details tab:
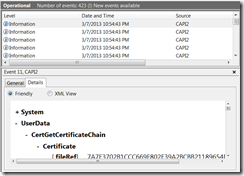
Here we can see what was passed into a given into that API call, we can see what certificates we passed in by the calling application, what settings they chose when making that call:
Some other things you can see in this particular API call include what the disposition of the call was and of course what certificate chain was built.
Every major API in CryptoAPI has logging similar to this, you get to see what is passed in and what came out. Additionally major “objects” are sometimes logged as well, for example here is an event showing a certificate that CryptoAPI was operating against:
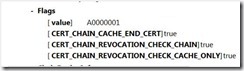
Another very useful API to be able to look at is CertVerifyRevocation, this will be logged in this fashion:
Some of these events include references to temporary files, for example in this case you see:
This is a CRL for the “GlobalSign PersonalSign 1 CA – G2”, its stored in the Time Valid Object Cahce (TvoCache), you can look at this cache with the “certutil –urlcache” command.
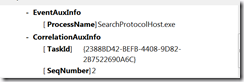
The events will all tell you which application was the caller and if they are part of a sequence of tasks you get enough information to correlate them and put them in order.
I won’t go through all of the events but as you can see this is super valuable when trying to figure out – Why did that application do that?!
As you might imagine this logging can slow things down and produces a bunch of data so be sure to turn it off when you are done.