In an earlier piece, ‘The Limitations of Audits,’ we explored how traditional compliance frameworks often fall short, functioning as point-in-time assessments rather than drivers of continuous security practices. Building on that foundation, and expanding on our exploration in ‘When AI Injects Liquidity Into Skills: What Happens to the Middle Tier?’, let’s examine how AI is poised to transform this landscape by introducing “skill liquidity” to compliance and auditing.
The High Price of Illiquid Expertise: Manual Bottlenecks in Compliance Today
As I’ve lamented before, the real cost of traditional, “illiquid” approaches to compliance expertise is staggering. In WebTrust audits, for instance, audit teams frequently report not having “enough time to look at the big picture” because their efforts are consumed by manual, repetitive tasks. Approximately 5-10% of an entire audit engagement – which can range from 350 to well over 1,500 hours for the audit firm alone – is often dedicated just to mapping organizational policy documents against standard templates. Another 15-20% of those hours are spent scrutinizing core operational processes mandated by frameworks, such as user access lifecycles or system change logs.
These percentages represent an enormous drain of highly skilled human capital on work that is largely automatable. And these figures only account for the auditors’ direct engagement. The true cost multiplies when you factor in the mountain of preparation by the entity being audited and subsequent review by third parties. The fully loaded headcount costs across this ecosystem for a single audit cycle represent a heavy tax on expertise that remains stubbornly “frozen” in manual processes.
First-Wave Automation: A Trickle of Skill Liquidity, or a New Kind of Friction?
The first wave of automation has arrived, with tools like Vanta and Secureframe offering streamlined pathways to certifications like SOC 2 by generating policy templates and automating some evidence collection. For many organizations, especially those with simpler, cloud-native environments, this has made basic compliance more accessible, a welcome “trickle of skill liquidity” that helps get a generic certification done in record time.
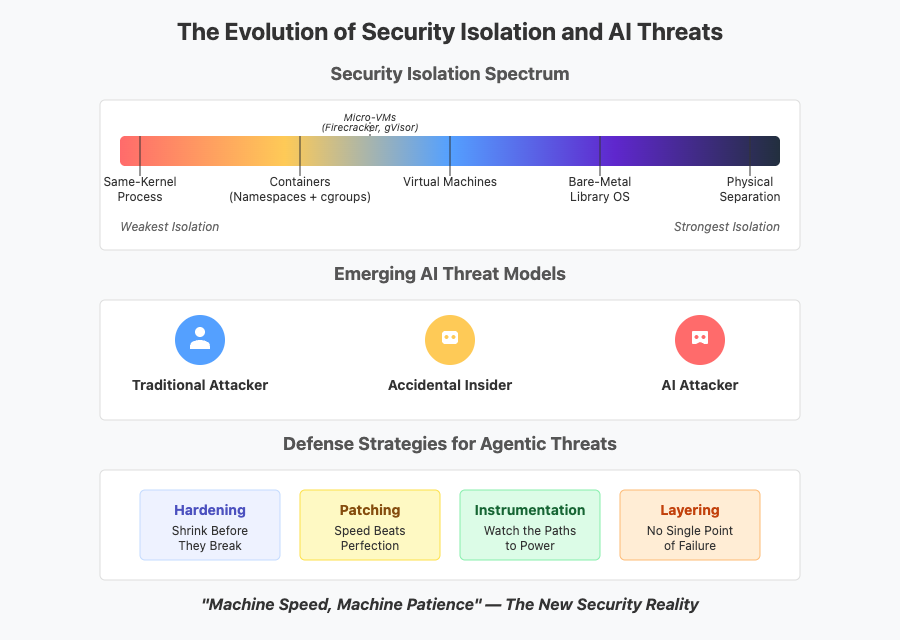
However, this initial wave has inadvertently created what we might call “automation asymmetry.” These tools predominantly empower the audited entity. When a company uses sophisticated automation to produce voluminous, perfectly formatted artifacts, while auditors still rely on largely manual review, a dangerous gap emerges. The truth risks getting lost in these “polished milquetoast” audits. The sheer volume and veneer of perfection can overwhelm human scrutiny, potentially masking underlying issues or a compliance posture that’s merely superficial. The audit can devolve into a review of well-presented fiction rather than an unearthing of operational fact.
Unlocking True Skill Liquidity: Intelligent Systems That Make Deep Compliance Knowledge Flow
To move beyond surface-level automation or basic Large Language Models (LLMs), we need intelligent compliance systems – sophisticated platforms designed to embed and scale deep domain knowledge. This isn’t just about processing text; it’s about an AI that understands context, relationships, history, and the intricate rules of specific compliance frameworks from the perspective of all stakeholders. Indeed, this drive to embed and scale specialized knowledge through AI is a significant trend across industries. For instance, leading professional services firms have been developing proprietary generative AI platforms, like McKinsey’s Lilli (announced in 2023), to provide their consultants with rapid access to synthesized insights drawn from vast internal knowledge bases, effectively enhancing their own ‘skill liquidity’ and analytical capabilities. Such systems, whether for broad consulting or specialized compliance, require:
- An ontology of expertise: Encoding the structured knowledge of seasoned auditors—controls, their intent, interdependencies, and valid evidence criteria.
- An ontology of documents: Understanding the purpose and interplay of diverse artifacts like System Security Plans, policies, vulnerability scans, and their connection to the compliance narrative.
- Temporal logic and change tracking: Recognizing that compliance is dynamic, and analyzing how policies, controls, and evidence evolve over time, identifying drift from baselines.
- Systemic integration: A cohesive architecture of LLMs, knowledge graphs, rule engines, and data connectors that can ingest, analyze, and provide auditable insights.
This approach transforms an AI from one that simply helps prepare artifacts to one that can critically assess them with genuine understanding – a crucial shift towards making knowledge truly usable (a concept we delve into in ‘From Plato to AI: Why Understanding Matters More Than Information’ ) – making that deep compliance knowledge flow across the ecosystem.
Liquidating Rote Work, Elevating Human Expertise: AI’s Impact on Audit Value and Integrity
When auditors and program administrators leverage intelligent systems, the nature of their work fundamentally changes—a direct consequence of “skill liquidity.” The AI can ingest and critically analyze the (potentially voluminous and auditee-generated) artifacts, performing the initial, labor-intensive review that consumes so many hours. This liquidates the rote work, significantly impacting even the global delivery models of audit services, as routine document review tasks are often offshored for cost savings, can now be performed with greater consistency, speed, and contextual insight by these intelligent systems.
This frees up high-value human experts to:
- Focus on what truly matters: Shift from the minutiae of “collection, ticketing, whether there was testing involved, whether there was sign-off” to the crucial judgment calls: “Is this a finding or a recommendation?”
- Investigate with depth: Dive into complex system interactions, probe anomalies flagged by the AI, and assess the effectiveness of controls, not just their documented existence.
- Enhance audit integrity: By piercing the veneer of “polished” evidence, these AI-augmented auditors can ensure a more thorough and truthful assessment, upholding the value of the audit itself.
The New Compliance Economy: How Liquid Skills Reshape Teams, Tools, and Trust
This widespread skill liquidity will inevitably reshape the “compliance economy.” We’ll see:
- Transformed Team Structures: Fewer people will be needed for the easily automated, “liquid” tasks of data collection and basic checking. The demand will surge for deep subject matter experts who can design, oversee, and interpret the findings of these intelligent systems, and who can tackle the complex strategic issues that AI surfaces.
- Empowered Audited Organizations: Companies won’t just be scrambling for periodic audits. They’ll leverage their own intelligent systems for continuous self-assurance, drastically reducing acute audit preparation pain and eliminating those “last-minute surprises.” Furthermore, the common issue of “accepted risks” or Plans of Action & Milestones (POA&Ms) languishing indefinitely is addressed when intelligent systems continuously track their status, aging, and evidence of progress, bringing persistent, transparent visibility to unresolved issues.
- New Proactive Capabilities: With compliance intelligence more readily available, organizations can embed it directly into their operations. Imagine Infrastructure as Code (IaC) being automatically validated against security policies before deployment, or proposed system changes being instantly assessed for policy impact. This is proactive compliance, fueled by accessible expertise.
Trust is enhanced because the processes become more transparent, continuous, and validated with a depth previously unachievable at scale.
The Liquid Future: Verifiable, Continuous Assurance Built on Accessible Expertise
The ultimate promise of AI-driven skill liquidity in compliance is a future where assurance is more efficient, far more effective, and fundamentally more trustworthy. When critical compliance knowledge and sophisticated analytical capabilities are “liquefied” by AI and made continuously available to all parties—auditees, auditors, and oversight bodies—the benefits are profound:
- Audited entities move from reactive fire drills to proactive, embedded compliance.
- Auditors become true strategic advisors, their expertise amplified by AI, focusing on systemic integrity.
- Compliance Program Administrators gain powerful tools for consistent, real-time, and data-driven oversight.
The journey requires a shift in perspective. Leaders across this ecosystem must recognize the risks of automation asymmetry and the limitations of surface-level tools. The call, therefore, is for them to become true orchestrators of this new compliance liquidity, investing not just in AI tools, but in the expertise, updated frameworks, and cultural shifts that turn AI’s potential into verifiable, continuous assurance. This is how we move beyond the “polished milquetoast” and forge a future where compliance is less about the performance of an audit and more about the verifiable, continuous truth of operational integrity, built on a bedrock of truly accessible expertise.